SANS Holiday Hack 2021 Review
This past December, like the years before, I took part in the annual SANS Holiday Hack (affectionately called KringleCon). KringleCon is an excellent, free experience put on every year by SANS that hosts a variety of fun hacking and security challenges and informative talks. More than that, it also wraps the experience in a fun North Pole-themed narrative. This year’s had the reoccurring “villain” of Jack Frost attempting to host his version of KringleCon at the same time to upstage Santa. The talks and challenges are all top-tier, and I highly recommend that anyone interested in security or hacking give it a shot. Past year’s events and challenges are available at https://www.sans.org/mlp/holiday-hack-challenge/.
For the competitive-natured people out there, SANS offers a variety of prizes based on the completion of a walkthrough document. Anyone who submits a report, even if they don’t complete all the objectives, is entered into a drawing to win. Additionally, the best technical answer, most creative, and best overall answer are also selected. In the previous years, I had entered my report, but I was still learning a lot and the content of the reports was mediocre at best. So, this year I went into the challenge determined to at least give a good shot at one of the higher prize winnings. To that effect, I completed a 48-page detailed report, which is available at my GitHub. I believe I did a solid job walking through all the challenges and explaining the solutions, though the last challenge did stump me a bit.
Since I posted the full report up, I won’t be walking through each answer like I did last year. Instead, I want to talk through the general structure of the challenges, what I found interesting, and what I struggled with.
Narrative Challenges
The challenges provided in the engagement are split into 2 categories, the primary challenges that move the narrative forward and various extra challenges that, when solved, provide hints to help with the primary challenges.
This year there were 13 primary challenges.
| Challenge Title | Challenge Focus |
|---|---|
| 1) KringleCon Orientation | Pick up badge and WiFi Adapter |
| 2) Caramel Santiago | Decode the Flask cookie given to get the answer and path which changes each game or use OSINT. |
| 3) Thaw Frost Tower Entrance | Use the WiFi Dongle to adjust the temperature and open the doors. |
| 4) Slot Machine Investigation | Modify webpage request parameters to cause unexpected results. |
| 5) Strange USB Device | Analyze and decode a Rubber Ducky script to identify who may have left the USB behind. |
| 6) Shellcode Primer | Create shellcode programs for basic functionality like opening and reading a file. |
| 7) Printer Exploitation | Modify a printer firmware file to append a payload, using a Hash Extension attack to fool the signing process. |
| 8) Kerberoasting | Escape restricted login, and attack an Active Directory to gain access to internal private documents. |
| 9) Splunk | Solve a variety of Splunk query questions. |
| 10) Now Hiring! | Use SSRF to query an AWS endpoint for valid credentials. |
| 11) Customer Complaint Analysis | Review a packet capture to identify specific traffic. |
| 12) Frost Tower Website Checkup | Review a Node.js website to find authentication bypass and SQL Injection to gain access to internal database. |
| 13) FPGA Programming | Create an FPGA module that creates a square wave function output. |
Extra Challenges
Additionally, there were originally 11 extra challenges, however 2 more challenges were added in the middle of the competition to provide more details on the then newly discovered Log4j vulnerability.
| Challenge Title | Challenge Focus |
|---|---|
| CP: Logic Munchers | Solve various puzzles related to identifying True outcomes. |
| CP: Yara Analysis | Edit an executable to bypass Yara Rules. |
| CP: Exif Metadata | Query metadata of a file to see who tampered with it. |
| Arcade: The Elf Code | Complete 8 Python challenges. |
| CP: IPv6 Sandbox | Use Nmap and Curl in IPv6 context to find information in the network. |
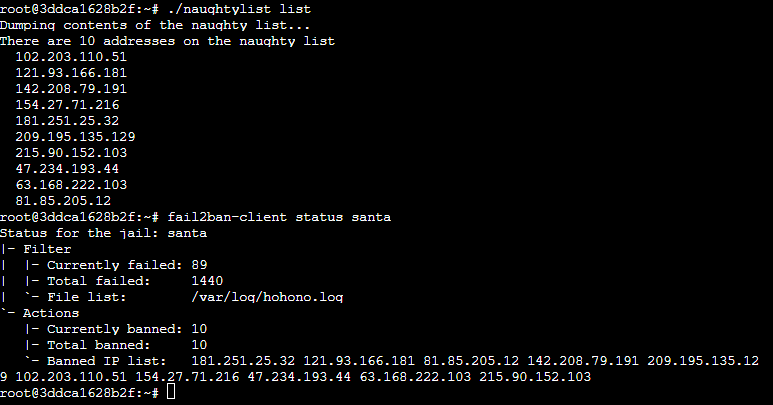
| CP: HoHo … No | Create a custom Fail2Ban setup to block malicious traffic. |
| CP: Strace Ltrace Retrace | Use strace and ltrace to identify what a program is missing to run correctly. |
| Sleigh: Holiday Hero | Modify cookie and Javascript to gain access to additional hidden functionality. |
| CP: Grepping for Gold | Use grep to answer various queries. |
| Elevator: Frostavator | Solve logic gates puzzle. |
| CP: IMDS Exploration | Walkthrough various queries against AWS metadata endpoint. |
| CP: Bonus! Blue Log4Jack | Walkthrough learning and defending against Log4j attack. |
| CP: Bonus! Red Log4Jack | Walkthrough attack path for Log4j. |
Since going through 26 unique challenges would take a significant amount of time (plus I did just that in the full report I shared), I just wanted to bring up a few of the most exciting challenges to me.
Narrative Challenge #8: Kerberoasting
This challenge was a welcome addition because it honestly felt the closest to what a real-world attack path looks like, and most of the steps replicated pieces I had done in my work engagements. The challenge starts with registering for a domain user account on a webpage. Once registered, you would be given SSH login credentials to what seems to be a restricted shell. Escaping that shell presents you with primary low-level OS access to a machine on the domain’s internal network. From there, a combination of reviewing SMB share contents, Kerberoasting (obviously), and network enumeration allow an attacker to escalate up to a privileged domain account and access the objective.
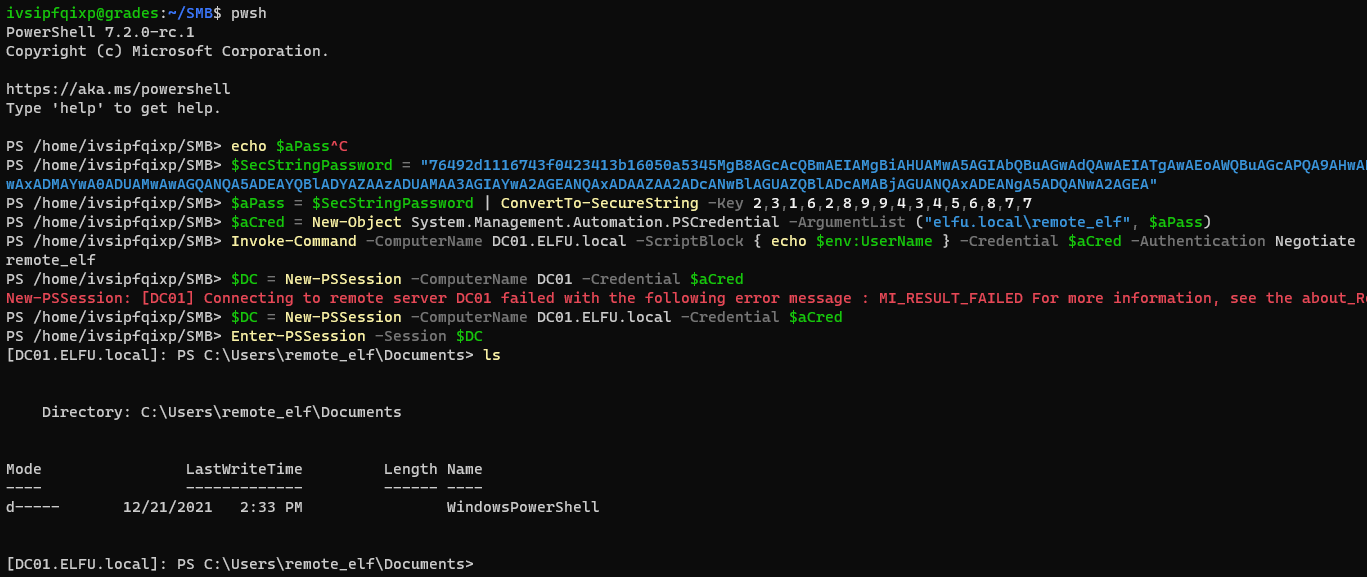
Now the objective is actually where this challenge gets a bit tricky. Attackers were challenged with reading a specific file on the network, with most people (myself included) assuming that we would need to reach Domain Admin to get that file. That assumption was incorrect and made the challenge much harder, as I spent a good while reviewing the wrong Active Directory groups, trying to find paths to DA. That experience was an excellent example of the path to sensitive information that doesn’t involve complete ownage of the environment.
Narrative Challenge #12: Frost Tower Website Checkup
Challenge #12 started by providing attackers with the complete source code for a website built with Express.js. Website development, especially with JavaScript, has never been a significant interest for me, so I can confidently say that this challenge forced me to learn quite a bit. Reviewing the source code revealed an authorization bypass based on a small non-default configuration made to the cookie library in use. With this authorization bypass, attackers had access to an endpoint that allowed for a custom SQL Injection UNION attack. To build a successful query, attackers had to work around conditions such as not including commas in the SQL statement, which took some creativity.
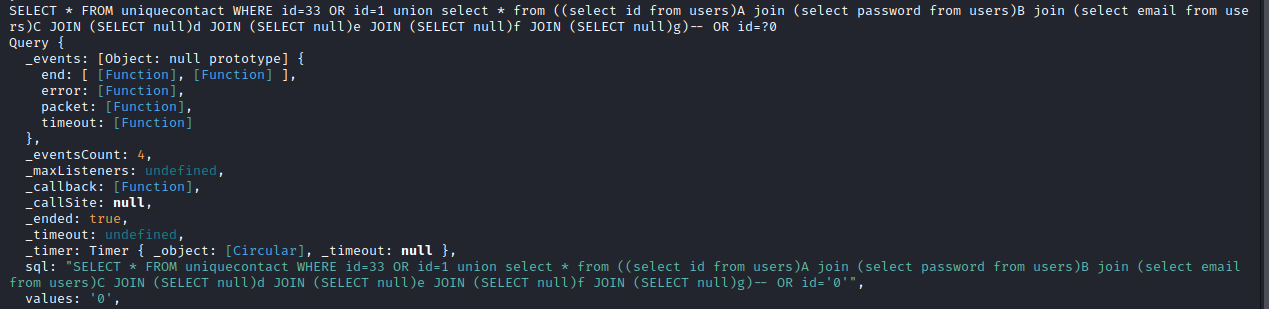
One of the most significant values that I pulled from this challenge was the benefit of actually taking the time to stand up a local environment that mirrored the target. By setting up a valid web server and SQL backend, I could easily log out all attempted queries and get the feedback needed to custom build the correct query for exploitation. Setting up local environments to match the victim has always been something that I have been lazy about doing, but working through this problem showed me the value it can bring.
Extra Challenge: HoHo … No
The above challenges focus on offensive red team tasks, which I am most familiar with. However, it’s essential, even for offensive folks, to take time to work through setting up and understanding the various defensive options. For this extra challenge, the task was to create a custom Fail2Ban setup to review an incoming log and ban malicious IPs. Fail2Ban is a solution that I was familiar with but never had to configure manually. The challenge wasn’t incredibly hard, but it required me to dive into the Fail2Ban documentation and understand how it operated entirely. This experience provided me with better insight into what it might require a client to configure a manual Fail2Ban solution.
Summary
While I highlighted a few of the challenges I personally really enjoyed, there is a wide range available for all skill levels and interests. I highly recommend that anyone interested in the space look at past events and challenges and give them a shot. The SANS Discord here and the write-ups being posted now that the challenge is over are wonderful sources of support, so don’t feel discouraged if you don’t know the solution right away. If anything that I have talked about sounds interesting, I highly recommend giving the challenge a try next December. Who knows, maybe you could be the one to create the winning report this year!